Privacy
In a survey of U.S. technology decision-makers, concerns over data security and privacy were considered to be the most important factors hindering acceptance and uptake of IoT solutions.
Underlying such concerns are a number of factors:
- Lack of transparency: many IoT devices operate in a manner where the end user consumer has no real visibility of the precise data streams such devices produce;
- Data subjects may be reluctant to share personal data: individual end user consumers (that is, data subjects) may not wish to share their personal data due to concerns over identity theft. They may have concerns about sharing data relating to location tracking on the basis that it might reveal personal behaviours. For example, “quantified self” things, such as a fitness tacker that maps the route and location of a jogger (and that, perhaps with consent, may share that data with other joggers using the same devices), might inadvertently reveal when a person is not at home and might be used by thieves logging into the system to target empty properties;
- Data “ownership” and use: businesses and data subjects may have no clarity over who, in an IoT ecosystem, has rights to use collected data, and what it will be used for. The processing of data within an IoT ecosystem relies on the intervention of a number of stakeholders (device manufacturers, data aggregators or brokers, application developers, social platforms, device lenders, etc.) who may share it with other parties without the data subject being aware of it;
- Differing regulatory regimes: data privacy legislation varies cross-jurisdictionally. While the EU General Data Protection Regulation (GDPR) creates a coherent body of law within the EU, the regime differs markedly from that in the U.S. and many other jurisdictions. Even in the case of the harmonised European regime, there are nonetheless several additional jurisdiction-specific data privacy frameworks to take into consideration. IoT solutions recognise no borders, resulting in compliance difficulties;
- Absence of prevailing standards: there is currently no generally accepted standard applying to the way in which an IoT device that collects data should be secured;
- Privacy by design: there is not as yet widespread adoption of IoT device and solution engineering to incorporate privacy-by-design;
- Rights of data subjects: by virtue of the limited size and lack of user interfacing inherent in many IoT devices, data subjects and users may not realistically be able to exercise their rights in relation to IoT-collected data (the legal implications are discussed below); andCross-correlation: data collected via IoT solutions can be cross-correlated with other data sources (from an IoT ecosystem or elsewhere) in ways that can breach privacy rights. For example, data derived from a data subject’s IoT-enabled toothbrush could be combined with data about the food that person eats from an IoT-enabled refrigerator, along with their IoT fitness-tracking device. Such data, perhaps in combination with IoT metadata like timestamps and location, together could reveal insights into the data subject’s overall health.
The rush to deploy IoT technology has outpaced the creation and implementation of security and privacy protections and standards for these devices. Marie-Helen Maras, Internet of Things: Security and Privacy Implications [2015] International Data Privacy Law, Volume 5, Number 2, page 100
Will every thing reveal everything?
Combining data sources from separate IoT devices, known by computer scientists as “sensor fusion”, can render greater insights than the sum of its parts. For example, data streams from, say, an IoT heartbeat monitor and an IoT device monitoring respiration can, in combination, show not only an individual’s typical exercise regime, but also whether that person uses alcohol, caffeine or illegal drugs (as each produces a separate biometric signature). However, such combining of separate data for new purposes has long been a problem under the data privacy laws of many jurisdictions.
There is a risk that, in combination with big data analytics and machine learning, IoT data will rapidly be able to reveal the most personal and intimate details, traits and habits about a human being – information that has never been made public by that person nor, with their consent, shared with anyone else, and all based on inferences drawn from the data.
Sensor fusion means that on the Internet of Things, ‘every thing may reveal everything’. Scott R Peppet, Regulating the Internet of Things: First Steps Towards Managing Discrimination, Privacy, Security, and Consent 93 Tex. L. Rev 85 2014 – 2015, page 93
A deeper dive into privacy concerns
IoT technology raises some more granular privacy concerns:
- Lack of control: data subjects may find themselves subject to third party monitoring due to the unobtrusive nature of the technology, and so lose control over the use and dissemination of their data. The data subject may not even be aware of the data processing being undertaken. The many data interactions and flows that occur may not be able to be understood or managed by the data subject using traditional end user data management techniques (such as GUIs, website terms and conditions, etc.), resulting in data use that completely departs from the purpose for which the data was originally collected;
- Lack of consent: a data subject using (or being exposed to) an IoT device may be unaware that the device is undertaking data processing. This means that the data subject may neither have been informed of the processing nor consented to it. If the data subject cannot realistically renounce features or services provided by an IoT device – say, because the device has no GUI or similar interface and there is no other mechanism to inform the data subject and get consent – then consent would similarly be called into question. IoT stakeholders will need to consider new ways of obtaining the data subject’s consent;
- Repurposing: data cross-matching and big data analytics mean that data collected by an IoT device could be used for secondary purposes beyond the scope of the original purpose for which the data was collected and processed. Third parties with access to the collected data could use it for a completely different purpose. Inferences could be drawn from the raw data when combined with other data sets. For example, in some jurisdictions, lenders are beginning to experiment with including IoT sensor data in credit assessments. Similarly, insurers could use information gleaned from an IoT fitness device to draw inferences with which to set premiums;
- Profiling: data collected via a number of IoT devices relating to a data subject could enable profiling of that individual to be undertaken, and reveal life and behavioural patterns, resulting in potential surveillance of hitherto entirely private spheres of life. For example, every human has a unique gait. With that information about a particular individual, a business in possession of anonymised fitness tracker data relating to thousands or even millions of individuals could identify the fitness data relating to that one individual, and so re-link that information to that person;
- Security: security issues relating to data collected by an IoT device extend beyond the device to the platforms upon which such data is stored, processed and transmitted. Lack of coordination between the various stakeholders can result in security weak points. The level of security of the whole ecosystem is limited to the level of security of the weakest component;
- Data amendment and deletion: the limitations inherent in IoT devices mean that it may not be possible to provide a data subject with the ability to access, edit and modify their data on the device itself. Separate tools (or user interfaces) may be required; and
- Notification: IoT devices do not normally include screens and keypads. They do not typically include other functionality to enable its manufacturer or supplier to communicate with an end user on an ongoing basis either, so there may be no way for them to notify the end user of: (1) the intended purpose for which collected data will be used; (2) security breaches; (3) vulnerabilities; or (4) the fact that the device is not being (or is no longer) updated. At the moment IoT device manufacturers typically provide privacy-related information in website-hosted privacy policies (rather than, say, in or on packaging or on the device itself). There may be no information at all directing the end user to a website’s terms of use, whether on the device or elsewhere. This is particularly problematic if the device’s activation does not depend on the user interacting with the relevant website.
Preliminary research suggests that robust anonymisation of Internet of Things data is extremely difficult to achieve … Scott R Peppet, Regulating the Internet of Things: First Steps Towards Managing Discrimination, Privacy, Security, and Consent 93 Tex. L. Rev 85 2014 – 2015, page 130
EU: GDPR
The GDPR raises certain issues that have particular application in relation to IoT ecosystems:
- The GDPR provides for obligations in relation to data security (essentially driven by the impact and likelihood of harm to the individual’s privacy and often fundamental rights), and there are significant fines for breach. Vulnerability of IoT devices, often deployed outside of a traditional IT structure and lacking sufficient security built into them, gives rise to the risk of data losses, infection by malware, unauthorised access to personal data, intrusive use of wearable devices, or unlawful surveillance, all of which must be addressed. Standards are not static, so future proofing / retirement must be designed into the system;
- Because of the large number of potential stakeholders in an IoT ecosystem (device manufacturers, data aggregators or brokers, application developers, social platforms, device lenders, etc.), it may be challenging to work out who, among them, is a data controller and who is a data processor. It will very much depend on the particular fact scenario. This matters because it is data controllers who will, for example, be responsible for responding to requests to exercise data subject rights;
- Users must remain in complete control of their personal data throughout the product lifecycle, and when organisations rely on consent as a basis for processing, the consent should be fully informed, freely given and specific. This may involve a number of different stakeholders;
- All controllers will need to communicate what data they collect and what they use it for and in many cases obtain their own granular consents – a real challenge for the user journey (particularly where the device would never traditionally have required registration to use);
- The issue of the place of establishment (relevant in relation to whether the GDPR applies to a particular set of data) is problematic in relation to IoT technology, which recognises no borders; and
- Rights of data portability under the GDPR require the provision of data and building an application programming interface (API) in certain circumstances. Where the IoT data is associated with an individual this will mean that competitors can offer services that utilise this data (as the individual can compel controllers to transfer the data to his/ her chosen service provider). Stakeholders in an existing IoT ecosystem will need to consider the implications of this in terms of competitor IoT platforms or data aggregators piggy-backing on what they might have considered to be a closed system.
For more information on the GDPR, see:
EU: draft e-Privacy Regulation
Once adopted by the EU, the EU draft Regulation Concerning the Respect for Private Life and the Protection of Personal Data in Electronic Communications (e-Privacy Regulation) will repeal the existing EU e-Privacy Directive 2002/58/EC. Among other things, the draft e-Privacy Regulation deals with data transiting across electronic communications services, and any subsequent use of such data.
Where electronic communications data is covered by the GDPR, the draft e-Privacy Regulation is intended to complement (rather than lower the level of) protection already offered by the GDPR by providing for more specific requirements.
In terms of IoT technology the draft e-Privacy Regulation raises a number of specific issues:
- The draft e-Privacy Regulation covers personal and non-personal data, so its protections could apply to all information transmitted by a device (e.g. meteorological data) via a commercially available network, and not merely information associated with an individual. The definition of “electronic communications services” includes machine-to-machine communications and IoT;
- The draft e-Privacy Regulation imposes a stringent obligation of confidentiality in relation to electronic communications data, backed up by significant fines (of the order provided for by the GDPR). This is a significant consideration in relation to stakeholders participating within an IoT ecosystem, where security may be very weak;
- There are practical considerations around applying the principle of confidentiality of electronic communications to machine-to-machine communications and IoT. Any interference (which includes processing and storing) with electronic communications is, except in limited circumstances, only allowed with the end user’s consent for specific purposes, including in relation to data which relates to, or are otherwise processed by, IoT devices;
- The draft e-Privacy Regulation contemplates that electronic communications network or service providers may be permitted to use the data in some limited circumstances without consent – for example, on one of the following grounds: (1) because it is technically necessary to transmit a communication; (2) for security; or (3) the use of metadata in order to detect faults, for billing, or to stop fraud. It will be important to determine the scope of such permitted use when the draft is finalised; and
- It will also be important to consider the grounds upon which an electronic communications provider may process end user data (particularly metadata, such as traffic data), and whether consent needs to be obtained. Such consent is of the type envisaged by the GDPR. Where an IoT ecosystem is used to provide services beyond mere transit of the data, such services would need to be specifically requested by the end user and their consent to the use of their data for such services obtained. This would certainly also apply to any subsequent change in use of the data already collected. This leads to a position even less favourable than the GDPR, so outside the narrow permitted exceptions all processing of personal data by the electronic communications or service providers must be consent-based. Stakeholders who are not responsible for data transmission are not caught by these requirements, so different requirements apply between the transmission and application layers.
Technical and organisational measures
Data privacy laws in many jurisdictions require that the data controller implements appropriate technical and organisational measures to safeguard the security of personal data. Such laws typically require the data controller to flow down these requirements in contractual relations with their suppliers who have access to such data.
Businesses will need to consider what the legal obligation to take appropriate technical and organisational measures to protect personal data means in the context of IoT technology. Purely technical solutions, implemented in the absence of a more comprehensive approach to information governance, may not be adequate.
The U.S. position
The U.S. Federal Trade Commission (FTC) published a staff report that, among other things, made recommendations to IoT stakeholders in relation to security, data minimisation, notice and choice. The FTC report noted that the FTC has no authority to pursue basic privacy enforcement proceedings (for example, in relation to privacy disclosures or consumer choice) in the absence of a specific showing of deception or unfairness (see U.S.: FTC Act, below).
The report recommended that Congress enacts broad-based (as opposed to IoT-specific) privacy legislation. The prospect of a U.S. federal privacy law has appeared to be more likely than in previous years, due to California having passed a new law which is similar to the European approach. As at the date of publication, it is impossible to forecast the terms of any such federal legislation.
The lack of a consistent approach in Europe and the U.S. in relation to IoT and privacy means that IoT stakeholders face the problem of contributing to an IoT ecosystem that will be subject to different privacy laws in the two largest markets in the western world.
The position in China
In China there are no data protection laws that are specifically related to IoT technology at the date of publication. The requirements under the China Cyber Security Law in relation to data protection apply to IoT technology as well as the relevant implementation measures for data protection.
Cyber security
Problems arising out of the interception, appropriation and corruption of data are exacerbated by IoT technology. Connected systems and information shared between devices inevitably present opportunities for criminal interception. In addition, unauthorised remote control of connected devices can give rise to complex legal questions about liability for what such devices may have done (when remotely controlled) if appropriate safeguards have not been put in place (see Liability).
Such activities may be undetectable within what may be open architecture technology or in circumstances where intrusion detection systems have not been implemented. Moreover, many IoT devices have no way of alerting the end user when a security problem arises, making it difficult for the end user to know that a security breach has occurred.
Typical IoT Attack Scenarios
- Against the network link between controller and actuator
- Against sensors, modifying the values read by them or their threshold values and settings
- Against actuators, modifying or sabotaging their normal settings
- Against the administration system of IoT
- Exploiting protocol vulnerabilities\
- Against devices, injecting commands into the system console
- Stepping stones attacks13
- DDoS using an IoT botnet
- Power source manipulation and exploitation of vulnerabilities in data readings
- Ransomware
Source: European Union Agency for Network and Information Security, Baseline Security Recommendations for IoT, November 2017, page 36.
EU: Cyber Security Directive
EU Directive 2016/1148 concerning Measures for a High Common Level of Security of Network and Information Systems Across the European Union (Cyber Security Directive) provides that EU member states must impose obligations of the type set out below in relation to “operators of essential services” (for example, utilities, such as energy and water; and transport, banking, financial markets, and digital infrastructure) and “digital service providers” (online marketplaces, online search engine and cloud computing services).
The Cyber Security Directive is subject to local implementation by EU member states. Depending on how it has been implemented locally (including by reference to published guidance), and the particular sector and infrastructure at issue, aspects of an IoT ecosystem (for example, a utility that uses IoT infrastructure) are likely to fall within scope, and stakeholders may be required to implement more stringent measures than required under the GDPR or draft e-Privacy Regulation (once implemented).
What does the Cyber Security Directive require?
Operators of essential services must:
- take appropriate and proportionate technical and organisational measures to detect and effectively manage the risks posed to the networks and information systems that they control and use in their operations; and
- notify the competent authority of incidents that have a significant impact on the continuity of the core services they provide.
Digital service providers must:
- identify and take appropriate and proportionate technical and organisational measures to manage the risks posed to the security of networks and information systems that they use; and
- notify the competent authority of any incident having a substantial impact on the provision of a service.
U.S.: Internet of Things Cybersecurity Improvement Act 2020.
The Internet of Things Cybersecurity Improvement Act 2020 was signed into law on December 4 2020. It is the first instance of explicit US federal regulation of IoT. The Act outlines the actions to be taken by the National Institute of Standards and Technology (NIST) and the Office of Management and Budget (OMB) to increase cybersecurity in relation to IoT devices used by federal government agencies.
The Act requires that devices supplied to the US government meet certain minimum information security requirements, as defined by NIST, including requirements concerning secure development, identity management, and patching and configuration management of IoT devices. Contractors and vendors to the US federal government must comply with vulnerability disclosure policies promulgated by NIST.
Although the Act does not apply in relation to consumers, its effect could be that IoT devices supplied to consumers might also comply with the Act’s requirements, as manufactures may find it difficult to have one device version and security protocols for the US federal government and others for other consumers.
U.S.: FTC Act
Some existing federal legislation is being used in IoT contexts. For example, section 5(a) of the U.S. Federal Trade Commission Act (FTC Act) prohibits “unfair or deceptive acts or practices in or affecting commerce.” The FTC has taken the view that lack or absence of reasonable security measures to protect consumers may constitute an unfair or deceptive practice under section 5, and has extended such oversight to aspects of IoT ecosystems.
U.S: California Senate Bill Number 327 (IoT Cybersecurity Law)
The Californian IoT Cybersecurity Law was passed into law by the state of California on 28 September 2018, and is said to be the first cybersecurity law regulating IoT devices passed by any of the U.S. states.
The legislation provides that, from 1 January 2020, a manufacturer of a “connected device” (in essence, an IoT device) must equip the device with a reasonable security feature or features that are appropriate to the nature and function of the device, appropriate to the information it may collect, contain or transmit, and designed to protect the device and any information contained in it from unauthorised access, destruction, use, modification or disclosure.
Such requirements are deemed to have been satisfied if:
- there is a pre-programmed password that is unique to each device; or
- the user is required to generate a new means of authentication before access to the device is granted for the first time.
The legislation does not confer a private cause of action on those who suffer harm as a result of a breach. Instead law enforcement agencies are given power to enforce it.
The new legislation has been criticised on the basis that it does not cover the whole range of IoT authentication systems that may or may not be called passwords.
U.S.: State Data-breach Notification Laws
Every U.S. state (and the District of Columbia) now has existing legislation providing for breach notification of personal information. The laws are generally of limited scope and many may not extend to a breach that results in disclosure of only IoT sensor data (where it does not include, for example, a user’s name or credit card account details).
China: the China Cyber Security Law
On 1 June 2017 the China Cyber Security Law came into force. It provides the following requirements for personal data protection:
- that where a product or service (for example, a IoT product / service) has the function of collecting a user’s information, the provider shall explicitly notify the user and obtain its consent;
- any personal information and critical information collected and generated during the business operation of “critical information infrastructure” (CII) operators within China (for example, IoT product / service providers that are engaged in the business of public communication and information services, energy, transport, finance, public services and e-government affairs will be defined as CII operators under the China Cyber Security Law) must be stored in China and must not be allowed to be transferred abroad, unless any cross-border transfer is made on the grounds of business necessity and has passed a security assessment by both a competent authority and the relevant CII operator; and
- the IoT product / service provider must not collect personal information irrelevant to the product / service provided by it.
China: draft Information Security Technology – Personal Information Security Specification
On 1 February 2019 the PRC State Administration for Market Regulation and the PRC Standardisation Administration jointly issued a draft Information Security Technology – Personal Information Security Specification. The draft Personal Information Security Specification is an updated version of an earlier specification, which had become effective on 1 May 2018. The updated version further implements requirements of personal data protection under the China Cyber Security Law.
The draft Personal Information Security Specification provides:
- that, where a product or service contains multiple business functions (for example, as in the case of an IoT ecosystem with multiple stakeholders) and each of the business functions requires the collection of personal data, the data collector shall not bundle the collection of personal data and require the personal data subject to give consent for personal data collection by one-time authorisation for all such functions; and
- for certain rules in situations where personal data is collected for a third party product or service (for example, those third parties higher up in an IoT ecosystem who wish to process the collected data gathered lower down) that has been incorporated or inserted into the master product or service. In such situation the data controller of the master product or service must:
- notify the personal data subject of the source of the third party product or service;
- establish a data security management mechanism for incorporating the third party product or service;
- supervise and monitor the third party to strengthen the security and protection of personal data; and
- request that the third party obtains consent for collecting the personal data following the rules and requirements of the Personal Information Security Specification.
Who “owns” the sensor-generated data?
IoT ecosystems produce highly valuable data. Stakeholders may wish to assert rights in relation to such data. End users of IoT devices may argue that the data is about them and should belong to them. Does exiting law confer such rights on stakeholders or end users?
The answer to this question depends on the jurisdiction at issue and the particular circumstances, including any contractual provisions. What follows is a consideration of the issue from a largely common law perspective in relation to non-personal data.
Under common law principles
The common law world appears to be divided over the question whether data can constitute property (that is, a thing capable of attracting proprietary rights). For example:
- the English criminal law case of Oxford v. Moss [1978] 68 Cr App Rep 183 is taken as authority for the principle in English law that there is no property in data as it cannot be stolen. On the other hand, the New Zealand Supreme Court in Jonathan Dixon v R [2015] NZSC 147 has held that digital files were property; and
- while a recent case in the English Court of Appeal took the view that a lien does not subsist over a database (Your Response Ltd v Datateam Business Media Ltd [2014] EWCA Civ 281), this can be contrasted with Thyroff v Nationwide Mutual Insurance Co 8 NY 3d 283 (NY 2007), in which the Court of Appeals of New York held that, although electronic records were intangible rather than tangible property, the tort of conversion (a right of action in respect of property) should apply to them.
Whether or not there are rights in data per se, rights and obligations do arise in relation to data. What follows are some examples.
Intellectual property rights: IoT-generated data
- Database rights: of the intellectual property rights potentially of use to IoT stakeholders (whether asserted against another stakeholder or against an end user), the specialised database protection regime (available within the EU) provides the strongest protection for data sets arising via an IoT ecosystem. The regime has some limitations. Case law in Europe, for example, may mean that the maker of a database who was also responsible for the creation of the underlying data cannot rely on the investment involved in data creation, but only in the investment involved in creating the resulting database. The creation of data itself might inevitably result in a database without additional investment of effort. In such a situation the creator of the data may struggle to avail itself of the protection of the database right. However, given its focus on investment rather than originality, the EU database right may still provide protection. The database maker must be able to demonstrate significant investment in obtaining, verifying or presenting the data in question. (Furthermore, the maker of the database must be a habitual resident of the EU, in the case of an individual or, in the case of a company, must have their registered office, central administration or principal place of business in the EU and its operations must be genuinely linked on an ongoing basis with the economy of a member state of the EU);
- Copyright: while copyright provides some protection for databases, in many jurisdictions it provides little comfort for those who have invested in the collection and creation of data sets created via IoT technology. Common cross-jurisdictional themes in relation to copyright include a requirement that the creator of a database can demonstrate effort in selecting and arranging data (rather than, as may be the case with many data sets, merely collecting it) and the identification of the particular human authors who are responsible for that independent intellectual effort;
- Patents: advancements in relation to IoT devices, networks, and methods of operation may sometimes be patentable in some jurisdictions. Although computer programs and business methods are not protectable per se, computer-implemented inventions may be patentable if they are new, inventive and make a technical contribution;
- Confidential information: the law of confidential information (or trade secret law in the United States, and the EU Trade Secrets Directive, in the case of Europe) may offer some legal protection to data sets created via an IoT ecosystem and used by a business for its own internal business affairs. On the other hand, where exploitation of the data extends beyond use for internal purposes to on-selling to third parties, it may be more difficult to demonstrate that such information is in fact confidential. For example, it may be difficult to satisfy a court that a data set is truly confidential if any third party can obtain access to that information provided that it pays a fee to the "owner" of the information. Much will depend on the treatment of the data after it has been initially acquired.
Contractual provisions
Contractual terms and conditions may provide for ownership of IoT-generated data, but are often silent on the issue. Research has established that, if terms and conditions are supplied at all in relation to IoT devices, they seldom provide for a privacy policy in relation to data collected by such device, nor information about what data the device will generate, where it is to be stored, whether such data can be corrected or erased, what the data will be used for and who owns the intellectual property rights (or other rights) to commercially exploit such data. IoT stakeholders need to address such shortfalls as a matter of priority.
The position of end users
If contractual provisions do not provide for who has rights to data as between an end user and a particular IoT stakeholder, the latter may face arguments that the data is somehow owned by the end user. Where the end user is a human (and not, say, a company), the end user will not be able to rely on data privacy laws to give it access and rectification rights where the data is not personal data. Data privacy rights do not generally override intellectual property rights.
Relying on the same kinds of arguments in relation to intellectual property rights that are available to IoT stakeholders is likely to be highly problematic for an end user, especially because the data in respect of which an IoT stakeholder may assert ownership may be quite different in form or substance from the raw data that an end user’s IoT device generated.
An end user might seek to argue that the raw data generated by its IoT device is its own confidential information, but this would very much depend on the facts. In any event, an IoT stakeholder would typically respond that it has an implied licence to use such data in respect of the service offered, if it is not actually the owner.
Intellectual property rights: non-data aspects
Putting IoT-generated data to one side, an IoT ecosystem consists of a range of other elements within which intellectual property rights may subsist:
Copyright and interoperability
- In parallel to copyright covering the content of data sets, source codes and object codes in IoT ecosystem software may also attract copyright;
- Interoperability in relation to an IoT ecosystem can give rise to copyright issues because achieving interoperability can involve copying code. EU law provides for an exception to copyright infringement in relation to interoperability - allowing legitimate users of a computer program to reproduce and translate its code in order to make an independently-created computer program to become interoperable with it, so that the different components can work together;
- In contrast, in the U.S., interoperability in relation to software and IoT ecosystems can be problematic in terms of copyright law. For example, in Oracle America Inc. v. Google Inc., the U.S. Court of Appeals for the Federal Circuit held that Google’s copying of Oracle’s application programming interfaces (APIs) infringed Oracle’s copyright in that software, and also rejected Google’s contention that its use met the statutory exception for “fair use”. As at the date of publication these decisions are on appeal to the U. S. Supreme Court; and
- Furthermore, in the U.S., copyright law contains only a narrow exception for certain types of reverse engineering of computer programs.
Software patents
- The development of an IoT ecosystem may lead to a significant increase of applications for software patents, which might allow owners to block use of technologies covered by these patents.
Standard-essential patents and patent pooling
- An outcome of adopting technical standards in relation to IoT might be that patents owned by different businesses are unavoidably infringed (as devices / networks are of necessity made compatible with the technical standards). Such patents are known as standard essential patents (or SEPs);
- In the case of telecoms industry, for example, SEP owners are entitled to a royalty stream from all other telecoms businesses that use the standard, on a fair, reasonable and non-discriminatory (FRAND) basis, in accordance with ETSI's rules;
- There has been a significant amount of patent litigation between telecoms businesses in recent years focussed on establishing whether the patent at issue is standard essential (and consequently whether a FRAND licence fee is owed to the patentee);
- Similar contentious scenarios are likely to arise in relation to IoT ecosystems. Unsurprisingly, key IoT stakeholders are keenly positioning themselves to structure the technical standards upon which IoT infrastructure will rely. However, unlike the telecoms industry (where there was a sector-wide consensus on the standards to be adopted), in the context of IoT, the position looks set to be fragmented; and
- New standards groupings have emerged, typically led by tech giants, which are formulating and promoting interoperability standards for IoT. Their members may well release all intellectual property rights (notably patent rights) relevant to the standards for other members to use on a royalty-free basis (or at least, on a FRAND basis). Each grouping hopes to create the best technical platform by which to attract other IoT stakeholders. Businesses involved in commercialising technology associated with IoT ecosystems will need to consider with which grouping(s) they should strategically ally (being mindful of litigation risks should there be an infringement of a patent owned by a member of a competing standards grouping).
Contracts for the supply or manufacture of equipment and services deployed in relation to IoT ecosystems will need to address the question of interoperability and changes to interoperability standards (including those required by law).
Liability
The difficulty of allocating liability … arises when a multitude of actors are involved in a particular process or environment. This is the case in the Internet of Things context, where a complex chain of interconnected products stems from different suppliers … Jacques de Werra and Evelyne Studer, Regulating Cybersecurity: What Civil Liability in the Case of Cyber-Attacks? 8 [2017] Expert Focus 511, at page 512.
Contractual liability
IoT interactions and data flows within an IoT ecosystem occur within a web of separately-owned or contributed technologies and a matrix of contracts or undocumented operating arrangements. Given the relative newness of IoT technology, many such interactions are unlikely to have been translated into clear contractual relations between owners / contributors of the technologies. This creates problems in terms of delineating both operational and legal responsibility between them, particularly given:
- the number of stakeholders involved where (typically) none of them has responsibility on an end-to-end basis for the particular application; and
any failures to flow security obligations right through an IoT component supply chain and across an entire IoT ecosystem.
Businesses:
- will need to consider the legal position when unauthorised intervention in relation to the operation of IoT devices occurs. Unless such risk is allocated contractually, affected parties will need to navigate complex laws (which exist in many jurisdictions) that deal with when a party can be exonerated from liability (whether in contract, tort, or otherwise) in connection with unauthorised third party intervention. Complicated issues of causation can arise where, say, a contractual breach or act of negligence (for example, a failure to put in place technical safeguards) is followed by an unauthorised third party intrusion;
- who use or rely on IoT technology will need to update internal IT usage policies to control the use of devices connecting to the IoT ecosystems; and
who supply IoT components or infrastructure should ensure that they do not expose themselves to liability for loss or corruption of data (and other losses that flow from
- a cyber intrusion incident) arising from their technology, and consider operational requirements (such as requiring end users to make regular data back-ups) to mitigate potential exposure.
In many jurisdictions, contracts can form even when they are not written down between stakeholders (or with end user consumers), and legislation or the courts may impose or imply terms and warranties into contracts.
For example, end user consumers in the United Kingdom may benefit from the provisions of the Consumer Rights Act 2015 in relation to:
- an IoT device as “goods”: here (among other things) the device must be of satisfactory quality, fit for purpose and installed correctly. It will not be regarded as conforming with the requirements if related “digital content” (see below) itself does not conform to requirements applicable to that content;
- digital content: suppose, for example, that an IoT device enables the end user consumer to access or use digital content (data) provided by the IoT device supplier – here the digital content will need to be (among other things) of satisfactory quality, fit for purpose and as described in the product documentation (or similar material); and
- mixed IoT (goods) and services: if the IoT device supplier supplies an IoT device to enable it to provide a consumer with a related service, the service itself will need (among other things) to be provided with reasonable care and skill and to conform to the relevant service description.
As the Consumer Rights Act 2015 is based in part on European Union legislation,[23] the laws of member states in the European Union typically include analogous requirements.
IoT devices and smart contracts
Emerging business models reliant on the operation of IoT devices (for example, IoT devices operating within a distributed ledger or blockchain implementation) sometimes envisage that such devices will be able to enter into contracts automatically, perhaps on an entirely “machine-to-machine” basis (so-called “automatic contracts” and perhaps smart contracts too) on behalf of an end user (for example, an automated supply chain for the provision of consumables or components operating within the Industrial Internet of Things).
Operating faults in relation to IoT devices concluding automatic or smart contracts could lead to unintended consequences (for example, over-ordering of products). This risk will need to be addressed contractually and operational safeguards implemented (for example, a requirement of order confirmation for orders falling outside the usual order pattern or outside other parameters).
For more information on the operation of smart contracts, see:
Product liability
In Europe:
- the General Product Safety Directive (GPSD) lays down general safety requirements that apply to all consumer products placed on the EU market, and states that all products marketed in the EU must be safe to use. (In the UK, the GPSD is implemented by the General Product Safety Regulations 2005 (the GPSR));
- the Product Liability Directive (PLD) guarantees the liability of the producer in the event of damage caused by malfunctioning products. The PLD lays down a common rule for liability without fault of producers at EU level. Where a defective product causes damage to a consumer, the producer may be liable even without negligence or fault on their part. The PLD applies to damage caused by death or personal injury, or caused to private property. (In the UK, the PLD is implemented by the Consumer Protection Act 1987 (CPA). Under the CPA, a manufacturer can be liable if a product is defective, a claimant has suffered damage, and there is a causal link between the defect and the damage. The CPA states that a product may be defective where its safety is not as persons are generally entitled to expect. Whether or not any instructions for use / warnings have been provided will be relevant to this).
Issues for IoT devices under the European product liability regime
Definition of “product”:
- under the PLD, a product is defined as “all movable objects, even when incorporated into another movable or into an immovable object. It includes electricity, primary agricultural products (products of the soil, of stock-farming and of fisheries, excluding products which have undergone initial processing - e.g. cutting, peeling and freezing fruit and vegetables) and game”;
- in the EU at least, the European Commission has expressed the view that, as far as they constitute “moveable” items, IoT devices and any other items containing intangible elements or presenting connectivity features qualify as “products”, and that defects in these products are covered by the PLD;
- however, it is the functionality of the intangible elements (software etc.) that is typically most important within an IoT device. This transfer of information may be considered a “service”. The European Commission’s view is that such service would fall outside the EU product liability and safety regimes. Therefore, “where damage is caused by the supply of erroneous data or by a failure to supply data, allocating liability may become unclear and claims potentially difficult to enforce”;
- such a view means that vendors might consider putting safety-critical functionality in the cloud in order to attempt to avoid product liability.
Concept of “producer” and liability:
both the GPSD and PLD introduce the concept of a “producer” into the EU regime on product liability, and it is the producer who is liable for unsafe or defective products;
A “producer” means:
- the manufacturer of the product (when he / she is established within the EU) and any other person presenting him / herself as the manufacturer by affixing to the product his/her name, trade mark, or other distinctive mark;
- when the manufacturer of a product is outside of the EU:
- the manufacturer’s representative;
- or if there is no representative established in the EU, the importer of the product;
- any other professionals in the supply chain in so far as their activities may affect the safety properties of a product.
- IoT devices throw up a number of unique questions when it comes to considering the liability of a producer of an unsafe or defective IoT device. Such products involve sophisticated interdependencies between hardware, software (whether embedded or not), networks and data. It may be the case that various elements of an IoT device fail and therefore various separate producers are at fault for the failure of one product. It may also be argued that separate products, communicating / transferring information to an IoT device by way of networks / software, could be caught by the third limb of the definition of “producer” (see above);
- these questions are becoming more pertinent as IoT devices become more sophisticated and more embedded into our daily lives, increasingly (for example) in the medical sphere. There have already been class actions brought in the U.S. for the failure of IoT devices, including from patients who received overdoses of medication / radiation due to a bugs in software that operated a medication / radiation-dispensing device. In defects such as these, isolating the root cause of the product failure can prove extremely difficult.
Adequate warnings and consumer information:
- under the PLD, a product is defective where it does not provide the safety which a person is entitled to expect, taking all circumstances into account, including: the presentation of the product, the reasonable use of the product, and the time when the product was put on the market;
- whether or not any instructions for use / warnings have been provided will be relevant to such an evaluation. As IoT devices become more sophisticated, and the technology more advanced, it will be more and more difficult to make information provided on products sufficiently clear to allow consumers to evaluate the security features of highly-technical products, and to understand the processes that allow them to function. Security of IoT devices is directly linked to their functionality and their safety of use. When considering which products to purchase, if given a choice, consumers are not always able to assess which is truly the more secure option. Furthermore, many manufacturers want to keep the security features of the products secret (because to provide them may make the product less secure and result in a loss of a “USP”) and therefore those producers who have invested in more secure products cannot easily differentiate themselves in the market;
- many manufacturers and distributors of IoT devices are still failing to provide adequate security, and are therefore creating opportunities for hackers to use such devices to harm innocent bystanders. An attack on an IoT device or an IoT ecosystem could cause malfunction of the device itself or errors in the related service, potentially causing both physical or economic loss. Data could also be destroyed or stolen.
Is there a risk that product liability might successfully be established in relation to an IoT stakeholder in such circumstances? Although the answer will vary jurisdictionally, many commentators have been sceptical about the viability of such product liability claims, for various reasons.
Future developments in relation to IoT devices and product liability
In light of the above issues, in Europe there are currently discussions on the adequacy of the GPSD and the PDL to face the challenges raised by new technological developments. In response the EU has produced a European Commission Staff Working Document: Liability for Emerging Digital Technologies. The ultimate objective of this is to launch a reflection on future developments regarding liability, in order to ensure equitable remedies and compensation to consumers, to offer legal clarity for producers, as well as to identify and avoid any potential disparities and fragmentation in the European Digital Single Market.
As at the date of publication, the European Commission is also consulting on changes that need to be made to the existing regime. These changes will take time to consider, however, and rebalancing of responsibilities between industry and consumers will be controversial.
IoT product liability issues
- In the EU, does the legal meaning of a product as defined by existing EU legislation extend to software and apps and the way that products communicate?
- In many jurisdictions it may be difficult or impossible to recover for pure economic loss relating to defective software that does not arise from physical harm;
- The proximate cause of damage may be tortious or criminal intervention by a third party (for example, hacking), making it more difficult to establish a causative link with the software manufacturer;
- More generally, is IoT technology a product or a service (or a mix) under applicable product liability legislation? Is software capable of being a defective product under the relevant applicable law?
- Is a product “defective” simply because it has no update facilities? Where the so-called “state of the art” exception is provided for in the applicable product liability legislation, does that exception apply in relation to issues such as patches and security upgrades, which may not have been available generally when an IoT device was originally launched?
- As a manufacturer, how do you warn about safety risks without compromising safety? If the consumer must have a mobile phone or an app in order to use the device, is it sufficient to give them safety information only on the phone or the app rather than at point of sale?
Should the idea of a “defect” also include a security objective on top of the safety one?
Tortious liability
Manufacturers and distributors of IoT devices already have ample notice within the IoT industry that such devices might have significant security defects and that insecure devices are frequently used to carry out cybersecurity attacks.
Once someone has published a tool that finds software vulnerabilities of a certain type, it would be difficult to claim they were not foreseeable. Similarly, if vulnerabilities are regularly found despite previous instances being fixed, then it is foreseeable that more are to come. Eireann Leverett, Richard Clayton and Ross Anderson, Standardisation and Certification of the “Internet of Things”, 22 May 2017, page 9
Operating faults relating to IoT devices might potentially cause economic loss, physical damage (such as malfunctioning causing a fire) or personal injury (as in the case of remote patient monitoring devices). Where this occurs, it may be difficult to establish who is responsible. Complex delineations of responsibility may be required between cooperating IoT stakeholders or with end users. This will be problematic where there are no contractual relationships between such persons, and in many jurisdictions such contractual relations will not in any event be sufficient to avoid liability in tort for negligence causing death or personal injury.
Legislation regarding (or requiring) technology protocols that effectively define the boundaries of operational responsibility may be considered appropriate to address uncertainty over liability. Courts in the meantime may face complicated factual scenarios in tort claims relating to IoT devices and IoT ecosystems, as it is likely that suppliers of all products and services interfacing with the malfunctioning IoT device (or an IoT platform more generally) will face claims, either from end users or other product or service suppliers, in the absence of contractually or legislatively-defined liability parameters.
Errors in IoT data
Data sourced from IoT devices or from another stakeholder in an IoT ecosystem may contain of errors. Such errors may arise, for example:
- at source (for example, defective IoT device sensors);
- through data transmission or interoperability problems; or
- as a result of processing errors in part of an IoT ecosystem.
Such errors may flow through to the outputs of data analytics processes in, say, an IoT platform, upon which a business's strategic and investment decisions may ultimately depend.
IoT stakeholders who on-supply such data, or who provide services dependent on it, could potentially face claims in contract, in tort (for example, for negligent misstatement) or for some other form of liability (this could include consumer claims based on statutory rights). Such businesses will need to ensure that they circumscribe their own liability on a back-to back basis where possible, or insure against the potential risks.
Autonomous decision-making by IoT devices
IoT devices will become more sophisticated over time. There is already a degree of automation in the way that actions are performed automatically by actuators, or data is sent, based on:
- externally received inputs (such as a change in temperature); or
- inputs from elsewhere in an IoT ecosystem.
Such actions do not require human intervention. New developments, however, have the potential to bring full-scale automated decision-making to an IoT ecosystem.
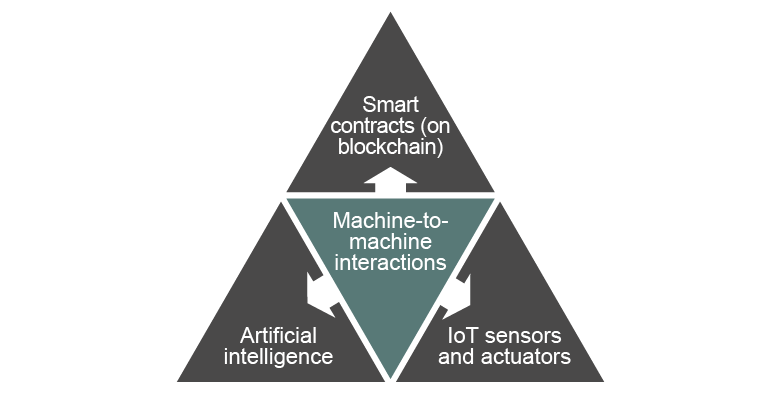
Elements of an autonomous IoT ecosystem
Artificial intelligence: embedding artificial intelligence (AI) within an IoT device (or the wider IoT ecosystem) has the potential to create additional value for those IoT stakeholders who control the data generated by the device or ecosystem, particularly given the amount of data an IoT ecosystem can make available to an AI system. AI can deliver many benefits, but there are also risks that will need to be addressed in any AI implementation. For more information, see our microsite, Artificial intelligence.
Smart contracts: even when not used in a contractual context, smart contracts can be used to automate industrial processes without human intervention. When combined with AI and an IoT device, they could be used to make decisions autonomously, operating within an Industrial Internet of Things, and then implement them both logically (electronically) and physically (through, for example, actuators).
For more information on smart contracts, see:
Regulatory
General regulation vs. sectoral regulation
In the absence of regulation or a contractual obligation, the burden of securing IoT devices lies with the end user. To what extent are governments and regulators likely to wish to shift that burden to other IoT ecosystem stakeholders? Where self-regulation is considered insufficient, the key issue is whether intervention should operate horizontally (that is, regulating the technology itself, across all sectors) or vertically (that is, sectorally, particular to specific industry sectors).
Two major global trading blocs, the EU and the U.S., currently take different approaches. Speaking generally, so far the U.S. at federal level has preferred self-regulation (except potentially in relation to supply of IoT technologies to the Federal Government itself in relation to IoT security), coupled with limited intervention using existing laws (see U.S.: FTC Act). For example:
- the U.S. Department of Homeland Security has promulgated Strategic Principles for Securing the Internet of Things, a set of non-binding principles and suggested best practices for IoT stakeholders to address IoT security challenges; and
- the FTC has advocated the use of a “Digital Standard” for multiple stakeholders to use as a testing system to evaluate whether IoT devices are meeting consumer expectations in relation to information security and privacy.
This approach has not been followed at state level by California (see Privacy).
The EU, on the other hand, appears to favour some degree of regulation over self-regulation, but has not come to a final position on whether that should apply across all sectors (that is, horizontally) or sector by sector (that is, vertically).
If a regulatory intervention on these technologies appears appropriate and necessary (in terms of new rules or an amendment to existing rules), it should be discussed whether that intervention should be developed in a horizontal or sectoral way … European Commission, Staff Working Document, Liability for Emerging Technologies, SWD (2018) 137, page 21
However, there are some early signs from the EU that a degree of horizontal regulation is already envisaged. For example:
- the EU Regulation for the Free Flow of Non-personal Data in the European Union is legislation that focusses on non-personal data, including non-personal data generated via IoT technology, regardless of sector. The regulation is a measure countering non-personal data localisation laws in the EU. Localisation laws might otherwise hamper the value of IoT technology in relation to non-personal data by forcing such data to be kept locally, as IoT operates without regard to borders. (On the other hand, there may be good reasons from a tax or regulatory perspective why a business may wish to keep its data housed locally); and
- the EU Digital Single Market Strategy mid-term review announced that the European Commission will consider the need to adapt the current legal framework to take account of emerging technologies such as IoT technology, especially from the angle of civil liability and under the Product Liability Directive and the Machinery Directive. A vertical approach did not appear to be envisaged.
The UK Position
The United Kingdom has adopted an intermediate position between self-regulation and intervention for the moment – advocating (at least in the case of consumer end users) moving the burden of having to secure IoT devices away from consumers, and instead ensuring that strong security is built into consumer IoT devices by design.
The UK Government seeks to do this primarily via self-regulation: a code of practice aimed primarily at manufacturers, IoT service providers, mobile application developers and retailers of consumer IoT devices and associated services. The UK government’s preference – like the U.S. - is therefore for the market to solve IoT security issues.
The UK Government has, however, received strong support for some form on regulation during the consultation on the draft code of practice. While it considers that many of the code’s guidelines are already aligned with current legislation (and that its objective is for appropriate aspects of the code to be legally enforceable), it has now commenced work to consider which aspects of regulatory change will be necessary. Following from such work, in 2019 the UK Government launched a Consultation on Regulatory Proposals on Consumer IoT Security. That Consultation seeks to define what baseline IoT security might look like, with a view to considering whether the following security requirements should be made mandatory in the UK:
- All IoT device passwords to be unique and not resettable to any universal factory default value;
- The manufacturer should provide a public point of contact as part of a vulnerability disclosure policy in order that security researchers and others are able to report issues; and
- Manufacturers should explicitly state the minimum length of time for which the product will receive security updates.
Some general regulatory requirements may apply
In the absence of specific IoT regulation (whether horizontal or vertical), there is a range of laws and regulations that will still need to be considered. A key issue is whether, or to what extent, they will apply in an IoT context. Examples include:
- In relation to IoT products and IoT-enabled machinery:
- Product safety: the EU General Product Safety Directive (2001/95/EC); and
- Machinery: the EU Machinery Directive (Directive 2006/42/EC of the European Parliament and of the Council of 17 May 2006 on Machinery, and amending Directive 95/16/EC (recast)); and
- IoT telecoms connectivity:
- Roaming: because many IoT devices are mobile and cross network and country boundaries, IoT connectivity providers operating in Europe will already be familiar with EU Regulation 531/2012 on Roaming on Public Mobile Communications Networks within the European Union (recast), and will need to monitor ongoing EU legal developments about the extent to which roaming regulations apply to IoT roaming; and
- Spectrum interference: IoT devices sometimes rely on radio frequency spectrum for connectivity. There is currently no consistent approach cross-jurisdictionally among regulators as to the treatment of allocation of what is often unlicensed or “white space” spectrum (such as that vacated by analogue television) for IoT needs. A key issue here will be the regulatory treatment of interference with already licensed parts of the spectrum. IoT stakeholders will face commercial challenges if a regulator in a given jurisdiction reserves to itself the power to force disconnection of IoT devices causing such interference.
Mobility
Many IoT devices are embedded in objects that move across national borders (for example, ships, trains, automobiles). By virtue of changes in location they may be subject to corresponding changes in the applicable legal and regulatory regime in respect of IoT technology and data generated. This presents challenges in relation to compliance, and will require a cross-border risk assessment.
Competition / anti-trust law
An IoT ecosystem has the potential to raise competition / anti-trust law concerns which may need to be considered by producers and distributors of devices:
- Standards setting: in setting standards for IoT devices, precautions need to be taken to ensure that standard setting does not facilitate sharing of competitively sensitive information or (at worst) facilitate price-fixing between competitors. Additionally, the process of setting standards will need to be designed to guard against discrimination against certain competitors or non-participants;
- Access to market “dominant platforms”: as a result of their retail activities, certain businesses may possess, or in some circumstances, gain a dominant position in the wholesale markets for data or access to consumers. Denying competitors access to data or access to consumers could entail a breach of competition law;
- Data aggregations: where businesses have control over data aggregations in relation to IoT devices, then restrictions on access – including exclusivity arrangements – can raise concerns under competition law about barriers to entry to the market and market foreclosure;
- Other abuses: other anti-competitive abuses that might potentially arise in relation to IoT products include discriminatory or predatory pricing, refusals to supply IoT devices, and / or tying or bundling; and
- Collaboration and consortia: data sharing and exchange is inherent in collaboration and consortia and may be compliant with competition law, subject to an assessment on the facts of each situation.
Tax
As IoT technology gives businesses the chance to transform, tax should be considered as part of the business planning phase in assessing the viability of an IoT offering.
This is because moving into an IoT ecosystem generally involves a transformation from selling products to selling services. Goods and services are often taxed differently – particularly where a supply of goods is made on a cross-border basis.
The tax system was developed with bricks and mortar businesses in mind. There is currently considerable focus on how the digital economy should be taxed. It is expected that the OECD will publish its proposals during 2020. The OECD’s 2019 update indicated that they were considering modifying existing transfer pricing rules and adapting the “nexus” principle to take account of user contributions to a business’s profitability.
Tax in user’s jurisdiction?
Since IoT businesses depend on the use of user data and the monetisation of user data, they could find themselves subject to any tax changes which result from the OECD’s proposals – and in particular, may find themselves subject to tax in their user’s jurisdictions even where the business has no other presence in that jurisdiction.
IoT technology also provides opportunities for tax authorities – as the technology could assist tax authorities with gathering information and assessing tax compliance.
Litigation, governing law and jurisdiction
Litigation in the context of an IoT ecosystem raises some practical and legal problems:
- Practical issues: from a practical perspective, as IoT devices have limited memory space, there is a risk that key facts and data (for example, when and why a safety-critical actuator activated or failed to activate) may simply be “over-written” by data relating to later interactions. This may be problematic for both claimants as well as device manufacturers – the latter may have no way of proving that the device operated as intended. Will IoT devices (for example, a device located in an inaccessible place) be able to be remotely interrogated? How would litigation “eDiscovery” searches be undertaken in relation to an IoT ecosystem where data could exist (if at all) in an entirely distributed basis across borders and multiple systems?
- Legal issues: because IoT data may be generated and stored in, or transmitted across, numerous jurisdictions, how will the governing law be determined in the case of a dispute, and whose courts are to have jurisdiction to hear the dispute? For some issues (for example, data privacy), laws exist (such as the GDPR) which can help to determine these matters. For other issues (or for a claim involving multiple issues), the courts in other contexts (for example, disputes in relation to the operation of the Internet; cloud computing; electronic contracting) have already had to deal with the problems that distributed systems (such as an IoT ecosystem) can give rise to. They do this by having regard to legislation, international treaties and a range of “conflict of laws” principles. Such an approach would apply equally to an IoT ecosystem. How such a body of law would apply in fact is the main challenge, given it may be very difficult and costly to determine what happened, and where, within an ecosystem of disparate parts involving numerous stakeholders whose interactions may be undocumented contractually.
